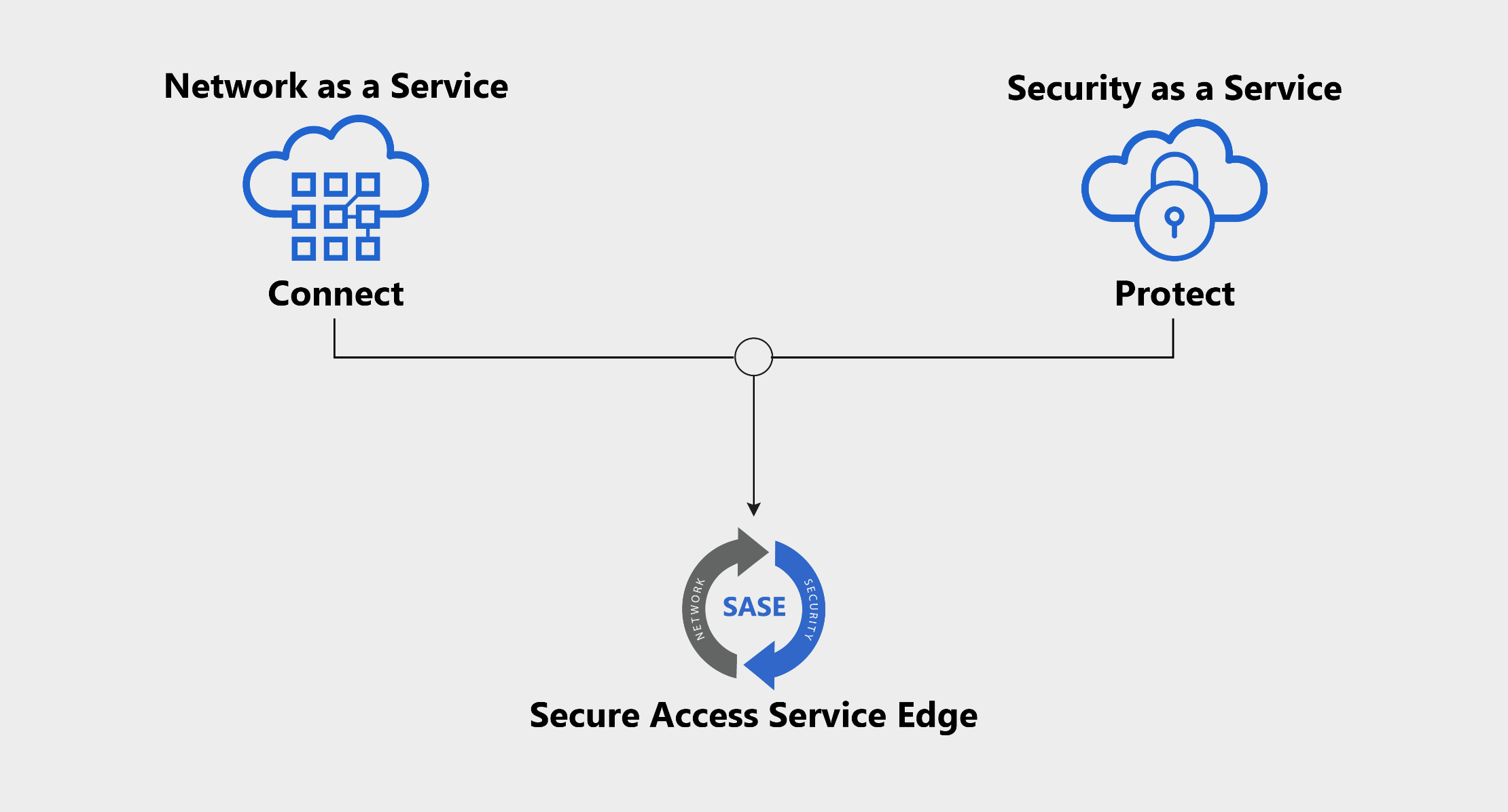
What is SASE?
SASE (Secure Access Service Edge) is a revolutionary architecture that merges network security and wide-area networking (WAN) capabilities into a unified framework. This innovative security solution is designed to meet the modern needs of organizations by providing a seamless approach to securing and managing network traffic, regardless of where users and applications are located. Traditional network architectures often struggle to keep up with the complexity and scale of today’s digital environments, especially with the increasing adoption of cloud services and remote work. SASE simplifies this by integrating essential security functions such as firewalls, secure web gateways, and zero-trust network access into a single service distributed globally. This comprehensive approach ensures that security policies are consistently enforced no matter where the network traffic originates or ends. By converging networking and security into a cloud-delivered model, SASE enhances security and simplifies IT infrastructure management, allowing for more agile and responsive operations.
Why Network Security Matters
The significance of network security in the current digital era cannot be emphasized. Organizations need to give the safety of their digital assets first priority due to the rise in cyber threats and data breaches. Various cybersecurity trends indicate an alarming rise in sophisticated cyber-attacks that can lead to devastating consequences for businesses regardless of size. For instance, ransomware attacks have become more frequent and sophisticated, often targeting critical infrastructure and large organizations. This has emphasized the need for resilient network security measures that respond promptly to emerging threats. Beyond preventing financial losses, robust network security fosters trust among clients and stakeholders, ensuring the organization’s reputation remains untarnished in an increasingly hostile cyber landscape. Furthermore, stringent network security practices help organizations comply with regulatory requirements, avoiding hefty fines and potential litigation associated with data breaches. Effective network security protects intellectual property and sensitive customer information, invaluable assets in maintaining competitive advantage and customer loyalty in the digital marketplace.
Benefits of SASE
SASE provides numerous advantages that can significantly enhance an organization’s network security posture. First and foremost, it improves security by offering comprehensive protection measures such as threat protection, secure web gateways, and data loss prevention. These features help mitigate risks and secure sensitive information from various cyber threats. Additionally, SASE reduces complexity by consolidating security and networking functions into a single service. This integration simplifies network infrastructure management, as IT teams no longer need to juggle multiple, disparate security solutions. The streamlined approach improves operational efficiency and reduces potential configuration errors that could lead to vulnerabilities.
Moreover, SASE enhances performance by delivering security services closer to the end-user through distributed points of presence. This reduces latency and ensures a more consistent and reliable user experience, making SASE an attractive option for modern organizations looking to bolster their network security. By unifying security and networking, SASE also facilitates seamless scalability, accommodating the dynamic needs of growing enterprises. As organizations expand, SASE can easily adapt to new security requirements and network complexity without requiring extensive hardware investments or complex reconfigurations. This flexibility makes SASE a cost-effective and future-proof solution for businesses of all sizes.
Integrating SASE into Your Network
Integrating SASE into a network requires meticulous planning and execution to ensure a seamless transition. To begin with, organizations must to carry out a thorough evaluation of their existing network architecture. This evaluation should pinpoint the areas where SASE might yield the most benefits and repair any current security holes. It is crucial to clearly understand network traffic patterns and specific security requirements unique to the organization. Such an assessment will form the foundation for a strategic integration plan.
Additionally, organizations must consider the interoperability of SASE with their current infrastructure. This involves evaluating whether their existing hardware and software are compatible with SASE components, ensuring minimal disruption during the integration process. Organizations can maximize the benefits of this advanced security framework by aligning SASE integration efforts with business objectives. Engaging all relevant stakeholders early in the process can facilitate smoother adoption and buy-in across the organization, ensuring that the transition to SASE is well-supported and effectively managed. It’s also advisable to conduct pilot tests and stage deployments to identify potential issues early and make necessary adjustments before full-scale implementation.
Best Practices for SASE Integration
- Conduct a thorough assessment: Evaluate your current network and security posture to identify gaps and areas for improvement. This step is crucial to understanding your organization’s specific needs and how SASE can address them effectively. Engaging with external auditors or employing internal security experts can provide a comprehensive view of your capabilities and areas where SASE can bring significant enhancements.
- Plan the integration: Develop a detailed plan that outlines the steps for integrating SASE into your network. This plan should include timelines, resource allocation, and potential risks. A well-structured plan ensures that all stakeholders are on the same page and that the integration process proceeds smoothly. Regularly update the plan to account for any identified gaps or adjustments, ensuring the project remains on track and aligned with the original objectives. Clear communication and documentation throughout the process are essential for maintaining transparency and managing expectations.
- Leverage expertise: Consult with industry experts and leverage best practices to ensure a successful implementation. Resources offer valuable insights and guidance on optimizing SASE deployment. Engaging professionals with experience in SASE integration can help navigate potential challenges and streamline the process. Utilize third-party consultants or participate in forums and industry groups to keep abreast of the latest advancements and methodologies in SASE deployment. Knowledge sharing and collaboration with peers undertaking similar projects can also provide practical insights and lessons learned.
- Continuous monitoring: Once SASE is implemented, continuous monitoring is crucial. Monitoring tools and processes should be robust to identify and mitigate potential security threats proactively. Regular audits and assessments will help ensure that the SASE architecture remains effective and up-to-date with evolving security landscapes. Advanced monitoring solutions such as threat intelligence platforms and AI-driven analytics can enhance the organization’s ability to detect and respond efficiently to sophisticated cyber threats. Also, fostering a continuous improvement culture and staying informed about emerging threats and technological advancements can help maintain a robust and resilient security posture.